38 min read
Accounts Payable Internal Controls: Best Practices & Examples
Discover how to implement robust controls in accounts payable processes to identify fraud, prevent duplicate payments, and ensure financial accuracy.
Accounts payable is one of the easiest places for errors and fraud to slip through. High invoice volumes, manual steps, and multiple people involved in approvals create room for mistakes, duplicate payments, and unauthorized transactions. These issues often go unnoticed until they show up in audits, cash flow problems, or vendor disputes.
Accounts payable internal controls exist to prevent this. They create structure around how invoices are received, reviewed, approved, and paid, so every transaction follows clear rules.
Below, we’ll break down what AP internal controls actually are, how they work in practice, and why they matter for financial accuracy.
What are accounts payable internal controls, and why do they matter?
What are the key components of an effective AP internal control system?
What is an accounts payable policy, and how do you create one?
How can you prevent duplicate payments in accounts payable?
What are the best practices for accounts payable controls in vendor management?
How should internal controls for invoice processing and approval workflows be structured?
What payment controls should be implemented?
How can technology and automation strengthen internal control over accounts payable?
What reconciliation and monitoring procedures are essential?
How does the month‑end close impact accounts payable controls?
How do you conduct an accounts payable internal controls assessment?
How do AP controls contribute to supply chain diversification and resilience?
Frequently asked questions
What are accounts payable internal controls, and why do they matter?
Accounts payable internal controls are systematic policies and procedures for managing payment processes in organizations. The primary goal of these controls is to ensure consistent accuracy, prevent fraud, and maintain the financial integrity of all vendor transactions.
What exactly are internal controls in accounts payable?
Internal controls in accounts payable (AP) form a complex framework of checks and balances governing the way a company approves, processes, and executes payments when it comes to its suppliers or vendors.
These controls cover multiple layers of verification, such as documentation requirements, approval hierarchies, and reconciliation procedures. These protective measures help block unauthorized transactions and ensure the company follows required accounting standards.
The accounts payable controls framework includes two major categories of actions: preventive and detective.
Preventive controls are:
- Segregation of duties between different staff members
- Authorization limits based on dollar thresholds
- Vendor verification and onboarding procedures
- Purchase order requirements before invoice processing
- Mandatory documentation for all payment requests
Detective controls are:
- Regular account reconciliations and audits
- Exception reports for unusual transactions
- Duplicate payment detection systems
- Variance analysis between budgets and actual spending
- Periodic reviews of vendor master files
Organizations apply internal controls using written policies, automated systems, and manual procedures. These controls help verify that each payment is legitimate, accurate, and properly authorized. A well-structured control environment is supposed to reduce the risk of duplicate payments, fraudulent transactions, and accounting errors that can damage financial statements or business relationships.
Why are AP internal controls critical for your business?
The critical nature of AP internal controls stems from their purpose to protect company assets while ensuring the accuracy of financial statements. Without proper controls in place, businesses are bound to encounter the following issues:
- Payment fraud schemes and embezzlement
- Duplicate payments and overpayments
- Cash flow mismanagement and liquidity issues
- Vendor disputes and damaged relationships
- Regulatory penalties and audit failures
The integrity of financial statements depends on the accuracy of AP reporting. The aforementioned controls exist to ensure that all liabilities are recorded correctly and that financial reports reflect the true state of obligations. A strong emphasis on accuracy is essential for management decision-making, as well as investor confidence and regulatory compliance.
Companies without strong internal controls often uncover many errors during audits, which can lead to restatements and, in some cases, loss of credibility. Strong controls also improve operational efficiency and vendor relationships. When payment processes are controlled and predictable, vendors get paid on time, and disputes become less frequent.
Organizations with strong AP internal controls tend to achieve:
- Better payment terms and early payment discounts
- Stronger supplier partnerships and preferential treatment
- Reduced processing costs and staff time
- Improved accounts payable forecasting and management
What are common accounts payable risks and controls to mitigate them?
Understanding accounts payable risks and controls is essential for protecting organizational assets. Weak AP controls expose organizations to a multitude of risks in different categories, such as:
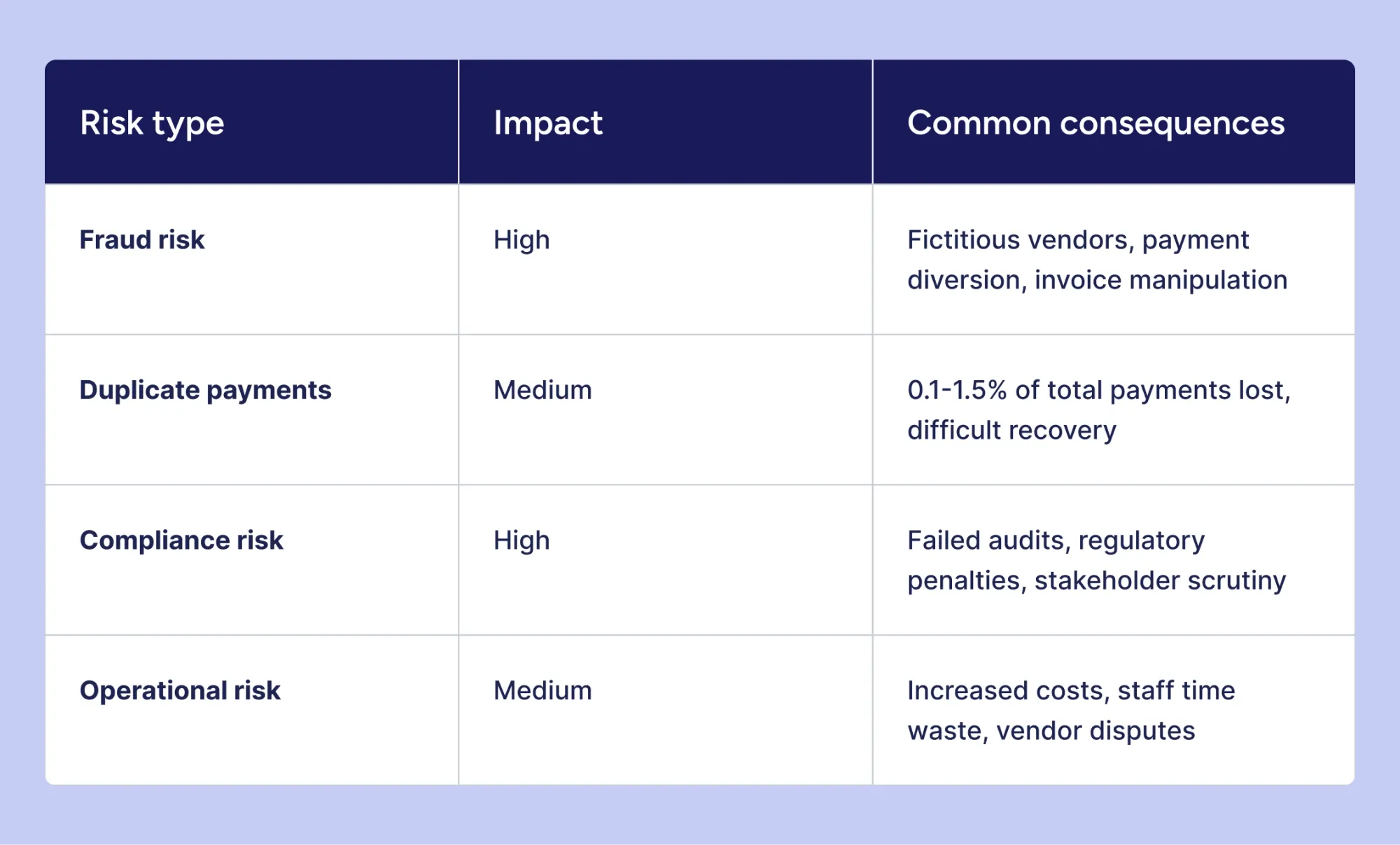
Fraud risk increases substantially whenever controls are absent or poorly implemented. Even the most common fraud schemes (fictitious vendors, invoice manipulation, payment diversion) result in losses of hundreds of thousands of dollars for businesses all around the globe.
The risk of duplicate payments increases when proper controls are missing. Companies without strong controls often pay the same invoice more than once, losing about 0.1 to 1.5% of total payments.
Weak controls also lead to numerous compliance and audit risks. Regulatory bodies demand adequate internal controls to ensure the accuracy of financial reporting. The absence of such controls might be the reason for failed audits, regulatory penalties, and an increase in scrutiny from stakeholders. Companies with publicly known weaknesses in internal controls may face difficulties securing financial insurance coverage.
When controls fall behind daily operations, teams spend more time fixing mistakes than doing strategic work. In these cases, staff members have to resolve payment disputes, research discrepancies, and correct errors instead of contributing to much more important business processes.
How do internal controls in accounts payable processes protect against fraud and errors?
Layered defense mechanisms are what make controls in accounts payable processes effective. They protect businesses against fraud or errors and create multiple checkpoints within the payment process. Key protection mechanisms include segregation of duties, three-way matching, authorization controls, and monitoring with reconciliation.
Segregation of duties ensures that no single individual controls every single aspect of a transaction. Fraud can only succeed if employees collude, since responsibilities like invoice receipt, payment processing, and reconciliation are separated.
A three-way matching process is supposed to verify that purchase orders, receiving documents, and invoices are all aligned before a payment is authorized. It detects discrepancies that might be an indication of fraudulent activity. Automated matching systems flag invoices that don’t correspond to received goods or approved purchases.
Authorization controls establish clear approval hierarchies based on departmental responsibility and transaction amount. High-value transactions require multiple approvals, which promotes accountability and lowers the risk of fraud.
Monitoring and reconciliation procedures are necessary to detect anomalies that could have slipped through various preventive control measures. Exception reports highlight different kinds of unusual patterns, including:
- Payments to new or unverified vendors
- Duplicate invoice numbers or amounts
- Transactions that exceed normal ranges or budgets
- Changes to vendor banking information
- Round-dollar payments or unusual payment frequencies
The audit trails created by internal controls allow investigators to trace transactions and easily identify the source of fraudulent activities or errors.
What are the key components of an effective AP internal control system?
An effective accounts payable internal control system consists of multiple interconnected components that prevent errors and fraud. Together, they create a comprehensive framework that addresses vulnerabilities at every stage of the payment cycle. Organizations must implement all key components (like accounts payable separation of duties and controls framework) in order to achieve maximum protection and operational efficiency.
What is accounts payable separation of duties, and why is it essential?
Accounts payable separation of duties is the practice of dividing critical AP tasks among multiple employees to prevent any single individual from controlling an entire transaction from start to finish. This fundamental control principle creates accountability and reduces opportunities for both fraud and unintentional errors. Separating duties ensures that any fraudulent activity would require collusion between several employees.
The core principle requires that different individuals record invoices, approve them, and process payments. The independence between these functions creates natural checks and balances that catch errors and deter fraudulent schemes.
Essential AP duty separations include:
- Invoice receipt and data entry – One employee receives and enters invoice information into the system.
- Invoice approval and authorization – A different employee with appropriate authority reviews and approves the invoice for payment.
- Payment processing and execution – Another employee prepares and processes the actual payment.
- Account reconciliation and review – A separate employee reconciles AP accounts and reviews transactions for accuracy.
- Vendor master file maintenance – An independent employee manages vendor additions, changes, and deletions.
- Check signing authority – Individuals who sign checks don’t approve invoices or process payments.
Organizations that fail to implement proper segregation of duties create environments where fraud can occur with minimal detection risk. If full segregation of duties isn’t feasible, small businesses can implement compensating measures—such as greater management oversight, mandatory vacation policies, and surprise audits—to help prevent fraud.
How does the three-way matching process work?
Three-way matching is one of the most important internal controls for invoice processing. It verifies that the purchase order, receiving report, and vendor invoice all match before approving payment. Three-way matching ensures the organization only pays for goods and services that were actually ordered, received, and properly invoiced.
Three-way matching document comparison:
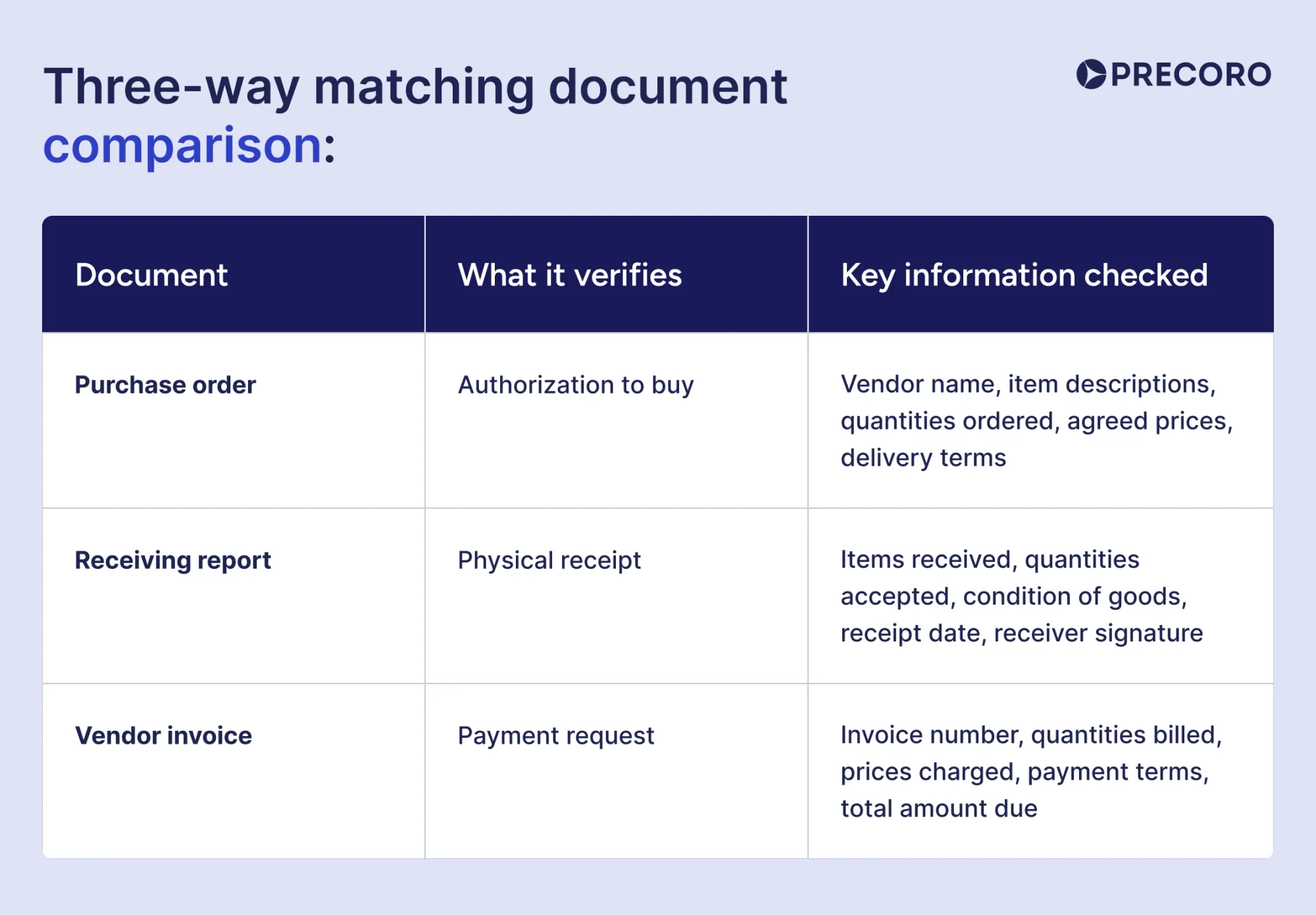
The accounts payable department receives the vendor invoice and retrieves the corresponding purchase order and receiving report from the system. Staff members compare all three documents to verify that quantities, prices, and descriptions match exactly. Any discrepancies trigger an exception process that requires investigation and resolution before payment can proceed.
Most modern AP systems automate three-way matching by electronically comparing data fields across the documents. The system flags mismatches such as quantity variances, price differences, or missing documents. Tolerance levels can be set to allow minor variances while escalating significant discrepancies for manual review. Organizations typically allow small differences, such as up to 5% in quantity or $50 in price, before a payment needs further approval.
The three-way matching process prevents several common fraud schemes, including fictitious vendor invoices, inflated pricing, phantom shipments, and duplicate billing. When combined with proper segregation of duties, it creates a robust defense against both internal and external fraud attempts.
What role does vendor master file management play?
The vendor master file is the centralized database that contains all approved vendor information, including names, addresses, tax identification numbers, payment terms, and banking details. It determines who is authorized to receive payments from the organization. If controls over the vendor master file are weak, fraudulent vendors could enter the system and receive unauthorized payments.
Vendor master file management prevents fraud by:
- Ensuring only legitimate, verified vendors are in the system
- Removing duplicate vendor records that lead to duplicate payments
- Maintaining accurate banking information to prevent payment diversion
- Controlling who can add, modify, or delete vendor records
- Requiring documentation and approval for all vendor changes
- Conducting periodic reviews to identify and remove inactive vendors
The greatest risk in vendor master file management is unauthorized additions or modifications. Employees with excessive or improper access can create fictitious vendors, change banking information to divert payments, or establish duplicate records. Organizations must restrict vendor master file access to specific employees who don’t have invoice approval or payment processing responsibilities.
Best practices require comprehensive documentation for new vendor setup, including completed vendor applications, W-9 forms, certificates of insurance, and verification of business legitimacy. Organizations often add controls like management approval, confirmation letters, and routine audits. Regular cleanup of the vendor master file removes inactive vendors and corrects duplicate records.
Organizations should establish procedures to verify changes to existing vendor information, particularly banking details. Fraudsters often send emails requesting changes to vendor banking details to redirect payments. Simple verification procedures, such as callback confirmation or written requests on vendor letterhead, can stop these attempts
Why is proper authorization and approval workflow necessary?
Proper authorization and approval workflows ensure that only legitimate business expenses are paid and that all spending follows budget limits and organizational policies. These workflows assign clear responsibility for reviewing and approving invoices based on dollar amounts and expense types. Without formal approval processes, organizations are at greater risk of unauthorized spending and fraud.
Authorization workflows create accountability and oversight by requiring budget owners to review and approve expenses before payment. The approval process verifies that goods or services were ordered, received as expected, and properly coded to the correct accounts. Approvers also confirm that pricing is reasonable, quantities are accurate, and the expense serves a legitimate business purpose.
Typical approval hierarchy by dollar threshold:
- Under $1,000 – Department supervisor or manager approval
- $1,000—$5,000 – Department head or director approval
- $5,000—$25,000 – Vice president or senior director approval
- $25,000—$100,000 – Chief financial officer or controller approval
- Over $100,000 – Multiple executive approvals or board authorization
The specific thresholds vary based on organizational size, industry, and risk tolerance. Companies should establish limits that balance control effectiveness with operational efficiency. Setting thresholds too low creates bottlenecks and frustration, while thresholds that are too high reduce control.
Modern AP systems enforce approval workflows automatically by routing invoices to appropriate approvers based on amount, department, account code, or vendor. The system prevents payment until all required approvals are obtained and creates an audit trail of who approved each transaction and when.
How can you implement effective audit trails?
Audit trails are detailed electronic records that document every action taken within the accounts payable system, including who performed each action, what changes were made, and when the activity occurred. These comprehensive logs enable investigators to reconstruct transaction histories when issues arise. That’s why effective audit trails are essential for resolving disputes and maintaining compliance with regulatory requirements.
The audit trail captures all significant events in the AP process from initial invoice receipt through final payment and account reconciliation. The system records user logins, invoice entries, approval decisions, payment processing, vendor master file changes, and system configuration modifications. Each record includes the user identification, timestamp, and description of the action performed.
Critical elements that audit trails must capture include:
- User credentials and authentication for all system access
- Invoice entry details, including amounts, vendors, dates, and account codes
- Approval actions with approver identity and decision timestamp
- Payment processing activities, including method, amount, and recipient
- Vendor master file additions, modifications, and deletions
- Changes to payment information, such as banking details or addresses
- System setting changes and security permission modifications
- Report generation and data exports
- Failed login attempts and security violation
Organizations must ensure that audit trail records can’t be altered or deleted by system users. The logs should reside in tamper-proof storage with restricted access limited to system administrators and internal audit staff. Regular reviews of audit trail data help identify unusual patterns, such as after-hours activity, excessive failed login attempts, or unauthorized access to sensitive functions.
Effective audit trails enable rapid investigation when fraud or errors are suspected. Investigators can search logs to identify who accessed specific vendor records, approved questionable invoices, or modified payment details. The ability to quickly trace transaction histories reduces investigation time and improves the likelihood of recovering fraudulent payments. Organizations should establish procedures for regular audit trail review and retention policies that comply with legal and regulatory requirements.
What is an accounts payable policy, and how do you create one?
An accounts payable policy is a formal written document that establishes the rules, procedures, and standards governing all payment activities within an organization. This policy serves as the foundation for internal controls by defining responsibilities, approval requirements, payment terms, and compliance obligations. The policy creates consistency across the AP function and provides clear guidance to employees about acceptable practices and procedures.
To create an effective AP policy, start by documenting existing processes and pinpointing areas that need standardization or improvement. Involve key stakeholders (finance leaders, department managers, and AP staff) in the development process. This collaborative approach ensures the policy doesn’t just meet regulatory requirements but also reflects day-to-day operations.
The policy document must incorporate best practices for accounts payable controls, including:
- Segregation of duties requirements
- Approval hierarchies and dollar thresholds
- Invoice processing procedures
- Payment methods and timing
- Vendor management protocols
- Exception handling processes
Additional sections should cover the following:
- Expense reimbursement policies
- Travel and entertainment guidelines
- Procedures for handling disputed invoices or payment discrepancies
Organizations operating in regulated industries or government contracting must also incorporate specific compliance requirements into their policies.
Once created, the policy requires formal approval from senior management or the board of directors to establish its authority within the organization. All AP staff and employees with purchasing or approval responsibilities must receive training on policy requirements and acknowledge their understanding in writing.
The policy should be easily accessible to all relevant employees and reviewed annually to stay up to date with changing business needs, regulations, and industry best practices. Regular updates keep the policy effective as a control tool.
How can you prevent duplicate payments in accounts payable?
Duplicate payments are a significant source of financial loss for organizations of all sizes. These errors drain cash reserves, damage vendor relationships, and indicate weaknesses in internal controls that require immediate attention. Understanding the causes and implementing robust prevention measures protects company assets and improves overall AP efficiency.
What causes duplicate payments in AP processes?
Duplicate payments occur when an organization pays the same invoice or vendor twice for identical goods or services. APQC benchmarking data indicates that even top-performing organizations experience duplicate payment rates of 0.8% of total disbursements, while organizations with weaker controls see rates exceeding 2%.
Common causes of duplicate payments:
- Manual data entry errors – Typographical mistakes or accidental double entry during high-volume processing.
- Vendor invoice resubmissions – Reminder invoices or statements processed as new invoices without payment verification.
- Duplicate vendor records – Multiple entries for the same vendor with slight name variations.
- Multiple submission channels – Invoices arriving through email, mail, portals, and fax processed by different employees.
- Weak verification processes – Insufficient checks before payment authorization.
The financial impact accumulates rapidly. A company processing $100 million in annual payments could lose between $100,000 and $500,000 to duplicate payments based on industry averages. Organizations that rely heavily on paper invoices and manual data entry experience error rates around 2% of total invoices processed.
Internal fraud schemes also contribute to duplicate payments. Employees with excessive access to AP systems may intentionally create duplicate invoices or collude with vendors to trigger multiple payments. Meanwhile, external fraudsters can submit altered invoices with minor changes to dates, amounts, or invoice numbers to exploit weak verification processes.
What controls can detect and prevent duplicate invoices?
Effective duplicate payment prevention requires multiple layers of controls that catch errors at different stages of the payment process. Organizations should implement both automated system controls and manual review procedures to create comprehensive protection. The controls must address the root causes of duplicate invoices while remaining practical and sustainable for daily operations.
These preventive controls stop duplicates before payment:
- Unique invoice numbering verification – System checks reject invoices with numbers already paid to the same vendor.
- Vendor master file cleanup – Regular reviews identify and merge duplicate vendor records.
- Centralized invoice intake – Single point of entry removes multiple processing channels.
- Three-way matching enforcement – Required matching of purchase orders, receipts, and invoices before payment.
- Standardized invoice submission – Vendors use consistent formats and submit through designated channels.
- Dollar amount and date matching – Flags invoices with identical amounts paid to the same vendor within specified timeframes.
Detective controls identify duplicates after entry:
- Exception reports – Daily reports highlight potential duplicates based on vendor, amount, date, and invoice number patterns.
- Aging analysis reviews – Regular examination of outstanding payables identifies duplicate entries awaiting payment.
- Vendor statement reconciliation – Monthly comparison of statements against payment records reveals duplicate payments.
- Payment history searches – Staff verifies payment history before processing each invoice.
- Audit trail reviews – Periodic examination of payment logs identifies unusual patterns.
Organizations should set tolerance thresholds that maintain control while keeping processes efficient. For example, flag invoices from the same vendor within 30 days if the amounts vary by less than 5%. The right thresholds depend on industry standards, vendor relationships, and past payment patterns.
How can automation help avoid payment duplication?
AP automation greatly lowers the risk of duplicate payments by replacing manual processes with smart detection tools. Modern AP systems build controls directly into workflows, ensuring key steps can’t be skipped.
Automated invoice processing systems capture data directly from invoices using OCR technology, which prevents manual data entry errors that cause many duplicate payments. The software extracts key fields, including vendor name, invoice number, date, and amount, then automatically compares this information against historical payment records. Advanced systems recognize variations in vendor names, identify similar invoice numbers with typos, and flag suspiciously similar amounts.
Leading AP automation platforms include:
- Precoro – Procurement centralization and automation platform with an AI-powered accounts payable module and an AP inbox.
- SAP Concur – Enterprise expense management software with duplicate detection.
- Coupa – Cloud-based procurement and AP automation system with AI-powered matching.
- Bill.com – Small to mid-size business payment platform with duplicate prevention.
- AvidXchange – Middle market AP automation platform with comprehensive controls.
- Tipalti – Global payment automation system with multi-entity support.
- Stampli – AP workflow automation software with collaborative invoice processing.
- Oracle NetSuite – Integrated ERP with built-in AP controls.
These platforms integrate with existing ERP systems and provide real-time duplicate detection during invoice processing. The automation workflows enforce approval requirements, maintain complete audit trails, and generate exception reports for suspicious transactions. Machine learning algorithms improve over time by analyzing historical patterns and adapting to each organization's unique payment characteristics.
Automation also prevents duplicate vendor records by standardizing vendor data entry and validating information against external databases. The systems flag potential duplicates during vendor setup based on tax identification numbers, addresses, and banking information. This proactive approach removes a major source of duplicate payments before invoices are ever processed.
What should you do if duplicate payments are discovered?
When duplicate payments are found, act fast to recover funds and prevent them from happening again. Organizations must follow a systematic approach that addresses the immediate financial impact while investigating root causes.
The recovery process involves the following steps:
- Identify and document the duplicate: Conduct a thorough review to confirm the duplication. Gather supporting documentation, including both invoices, payment confirmations, and bank statements. Document payment dates, amounts, and check numbers.
- Notify the vendor immediately: Contact the vendor with clear documentation showing both payments. Request an immediate refund or credit while maintaining professional communication to preserve the relationship.
- Negotiate recovery terms: Discuss options including full refund, credit against future invoices, or offset against outstanding payables. Document all agreed-upon terms in writing and request expedited resolution for large amounts.
- Update accounting records: Record the correction with proper documentation. Adjust accounts payable balances and ensure financial statements reflect accurate positions. Create clear audit trails of the entire recovery process.
- Investigate and prevent: Determine the root cause through process examination and system reviews. Address identified weaknesses through enhanced controls, training, or process improvements to prevent recurrence.
The recovery process can be time-consuming, and success depends heavily on vendor cooperation and how quickly the duplicate is identified. Organizations should track duplicate payment recovery as a key performance indicator and implement stronger preventive controls to minimize future occurrences.
What are the best practices for accounts payable controls in vendor management?
Vendor management and verification are critical components of accounts payable internal controls. Proper vendor oversight prevents fraud, ensures payment accuracy, and maintains compliance with regulatory requirements. Organizations must implement systematic processes for onboarding, verifying, and monitoring all vendors throughout the business relationship.
How do you establish a robust vendor onboarding process?
A robust vendor onboarding process creates standardized procedures for adding new vendors to the payment system. Organizations should implement the following workflow:
- Application submission – Department submits a formal vendor request with business justification and a vendor application form.
- Documentation collection – Gather required documents, including W-9 tax forms, certificates of insurance, and banking information.
- Verification – Confirm business legitimacy through independent checks of business licenses, tax identification numbers, and references.
- Segregation review – Ensure vendor setup personnel are separate from invoice approval and payment processing functions.
- Final approval – Obtain sign-off from accounts payable management and the requesting department before activation.
Automated vendor onboarding portals, like Precoro’s, streamline the process by allowing vendors to submit information electronically and track application status. The portal validates data entry, ensures all required fields are completed, and maintains audit trails of the entire onboarding workflow.

What information should be verified before adding a new vendor?
Organizations must verify multiple data points before activating a new vendor in the payment system. Essential verification requirements include:
- Tax Identification Number (EIN or SSN) – Confirm with the IRS database or request a W-9 form.
- Business registration and licenses – Verify active business status with state agencies.
- Physical address verification – Confirm through independent sources, avoid P.O. boxes for new vendors.
- Banking information – Validate through callback to vendor using independently sourced phone number.
- Insurance certificates – Verify coverage amounts and effective dates match requirements.
- Ownership and authorized signers – Document individuals authorized to receive payments.
- References and credit checks – Contact trade references for high-value vendor relationships.
The verification process should document all sources used to confirm information and maintain records of verification activities. Organizations should never rely solely on vendor-provided documentation without independent confirmation of at least the business registration and tax identification number.
How can you detect and prevent vendor fraud schemes?
Preventing vendor fraud requires layered controls that create multiple verification points throughout the vendor lifecycle. Organizations should implement callback verification procedures when vendors request banking information changes, using phone numbers obtained independently rather than from the change request itself.
Key prevention controls include:
- Require multiple approvals for new vendor setup and vendor information changes.
- Implement automated duplicate detection based on tax ID, address, and banking details.
- Restrict vendor master file access to designated employees who do not process payments.
- Conduct periodic audits comparing vendor addresses to employee addresses.
- Flag and review vendors with sequential invoice numbers or round-dollar invoices.
- Require vendor confirmation letters sent to registered addresses for new high-value vendors.
Exception reporting identifies suspicious patterns such as multiple vendors sharing addresses, bank accounts, or phone numbers. Organizations should investigate vendors that receive frequent payments just below approval thresholds, or that suddenly begin receiving significantly higher payment volumes.
What are the warning signs of fictitious vendors?
Fictitious vendor schemes involve creating fake vendors to divert company payments. Red flags that indicate potential fictitious vendors include:
- Address anomalies – P.O. boxes, addresses matching employee addresses, or multiple vendors at the same address.
- Payment patterns – Invoices consistently just below approval thresholds or frequent round-dollar amounts.
- Missing documentation – Lack of supporting documentation, contracts, or purchase orders.
- Sequential invoicing – Invoice numbers that follow perfect sequential patterns.
- Unusual vendor names – Vague business names, misspellings of legitimate vendor names, or names similar to employees.
- Banking red flags – Multiple vendors using the same bank account or account holder name not matching the vendor name.
- Contact information issues – Generic email addresses, cell phone numbers only, or unverified addresses.
Organizations should immediately investigate any vendor that matches employee information, including names, addresses, phone numbers, or bank accounts. Cross-referencing vendor master file data against employee records through automated reports helps identify these schemes before payments are processed.
How often should vendor information be reviewed and updated?
Vendor information requires regular review and maintenance to ensure accuracy and identify inactive or duplicate records. Organizations should conduct comprehensive vendor master file reviews at least annually, with more frequent reviews for high-volume or high-value vendors.
Quarterly reviews should focus on vendors with recent activity, confirming that contact information remains current and payment terms are accurate. The review process should flag vendors with no payments in the past 12–18 months and investigate whether they should be deactivated.
Organizations must establish procedures for vendor-initiated updates to critical information such as banking details, addresses, or ownership changes. These changes should trigger verification workflows that confirm the legitimacy of the update request through independent communication channels. Documentation of all changes and the verification performed should be maintained in the vendor file.
Automated reports can flag vendors requiring review based on inactivity periods, missing required documentation, or expired insurance certificates. Regular cleanup of inactive vendors reduces clutter in the vendor master file and decreases the risk of erroneous or fraudulent payments to obsolete vendor records.
How should internal controls for invoice processing and approval workflows be structured?
Invoice processing and approval workflows create the operational framework for ensuring that only legitimate, accurate payments are processed. Properly structured workflows balance control effectiveness with operational efficiency while maintaining clear accountability at every stage. Organizations must establish standardized procedures that all employees follow consistently.
What are the essential steps in the invoice approval process?
A standardized invoice approval process ensures consistent treatment of all payment requests and creates clear audit trails. Organizations should implement the following workflow:
- Invoice receipt – Invoices arrive through designated channels and are logged into the system with the receipt date and a unique tracking number.
- Data entry and validation – AP staff enter invoice details and validate key fields, including vendor, amount, date, and payment terms.
- Three-way matching – System compares the invoice to the purchase order and the receiving documentation, flagging discrepancies for resolution.
- Coding and allocation – The invoice is coded to the appropriate general ledger accounts and cost centers per the organizational chart of accounts.
- Approval routing – The invoice is routed to designated approvers based on amount, department, and account code per established workflow rules.
- Final review and authorization – Approvers verify accuracy, business purpose, and proper documentation before authorizing payment.
- Payment scheduling – Approved invoices are scheduled for payment based on due dates and cash management policies.
Automated workflow systems ensure these steps are followed, prevent invoices from skipping required controls, and maintain a complete audit trail.
Who should be authorized to approve invoices at different levels?
Invoice approval authority should be assigned based on organizational hierarchy and budgetary responsibility. Department managers typically approve invoices related to their departmental operations within established spending limits. These approvals confirm that goods or services were received as expected and serve legitimate business purposes.
Finance and accounting leadership approve invoices that exceed departmental authority limits or involve categories requiring specialized review, such as capital expenditures, professional services, or intercompany transactions. Executive approval would be required for high-value transactions, unusual expenses, or payments outside normal business operations.
Organizations must maintain current approval matrices that document who can approve what types and amounts of invoices. The matrix needs to specify primary and backup approvers to prevent processing delays when key individuals are unavailable for one reason or another. Approval authority should never extend to employees who also process payments, maintain vendor records, or perform account reconciliations.
How can you implement dollar threshold approval limits?
Dollar threshold approval limits must be clearly documented and set up in the system to enforce the approval hierarchy. Organizations should define approval limits that specify exact amounts and the number of approvals required at each level. The rules should also clarify whether thresholds apply per invoice, per purchase order, or per vendor.
System configuration should automatically route invoices to appropriate approvers based on the invoice amount without manual intervention. The workflow should escalate to higher approval levels when amounts exceed lower-tier limits, requiring multiple approvals in specific situations described in the policy. Organizations should establish exception processes for urgent payments that need expedited approval while maintaining proper controls.
Regular reviews of approval thresholds ensure that they remain appropriate as the organization grows and inflation impacts purchasing power. Companies need to analyze approval bottlenecks to identify whether thresholds are set too low and are causing unnecessary delays. Training programs help ensure all employees understand the approval limits and routing procedures.
What documentation is required to support invoice payments?
Strong internal controls for invoice processing require comprehensive documentation at every stage of the payment process. Proper documentation creates evidence of transaction legitimacy and supports audit requirements. Standard documentation requirements include:
- Purchase order – Original approved PO showing authorization to purchase goods or services.
- Receiving report – Confirmation that goods were received or services were performed as ordered.
- Vendor invoice – Original invoice with clear description, pricing, and payment terms.
- Contracts or agreements – Underlying contracts for service agreements or large purchases.
- Approval documentation – Evidence of proper authorization from individuals with spending authority.
- Exception approvals – Additional documentation for invoices processed outside standard procedures.
- Expense reports – Supporting receipts and business purposes for reimbursable employee expenses.
Documentation should be attached to invoices in the AP system, where it can be easily retrieved during audits or payment inquiries. Organizations must establish retention policies that specify how long payment documentation must be maintained to meet legal and regulatory requirements. Digital document management systems reduce physical storage needs while improving accessibility and search capabilities.
How do you handle invoices without purchase orders?
Invoices without purchase orders require additional scrutiny and alternative documentation to ensure their full legitimacy. Organizations should limit the types of expenses that can be processed without purchase orders to specific categories, including:
- Utilities
- Recurring services
- Subscriptions
- Professional fees
- Low-value office supplies
The approval process for non-PO invoices must require higher-level authorization than standard PO-backed invoices of similar amounts. Approvers should provide written justification explaining why the expense was necessary while confirming that goods or services were received. Alternative documentation, such as service agreements, contracts, or delivery confirmations, should be required to support the payment request.
Organizations should track and analyze non-PO invoice volumes to identify departments or expense categories where purchase order compliance is weak. Persistent processing of invoices without purchase orders may be a sign of inadequate planning, unclear policies, or deliberate circumvention of controls. Regular reporting to management on non-PO invoice trends helps enforce existing purchasing policies and also strengthens the overall control environment.
What payment controls should be implemented?
Payment controls serve as the last line of defense against fraudulent or incorrect payments. Strong payment controls protect cash assets, prevent unauthorized transactions, and ensure that payments reach legitimate vendors. Organizations must implement multiple layers of protection across all payment methods and channels.
What are the most secure payment methods for accounts payable?
Organizations should select payment methods based on security requirements, transaction characteristics, and vendor capabilities. Each payment method offers different security features and control opportunities:
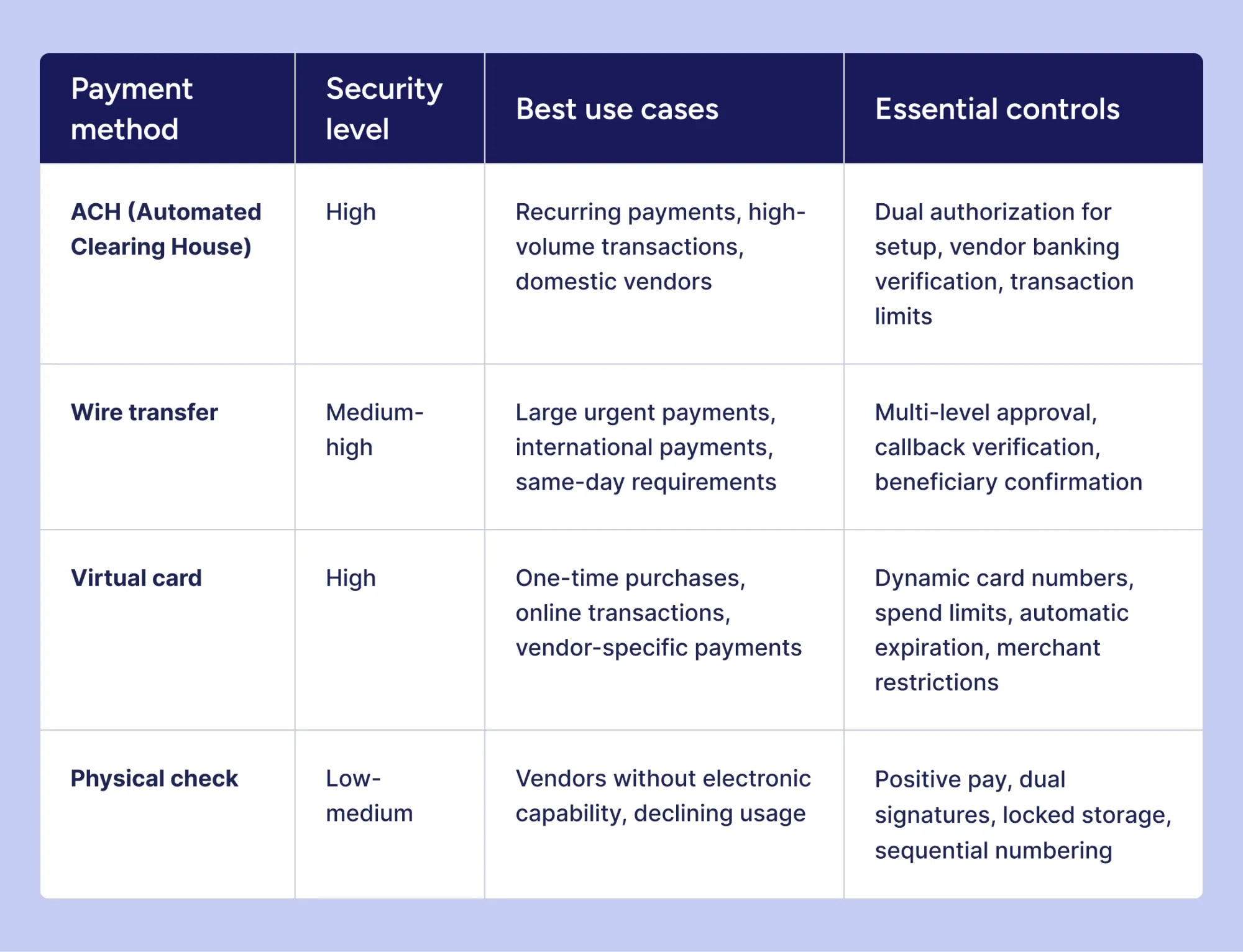
Electronic payment methods provide superior audit trails and automated controls compared to physical checks. Virtual cards offer the highest security through single-use numbers and built-in spending restrictions.
Organizations should establish policies that prioritize electronic payments and limit check usage to situations where alternatives are not available. Payment method selection should consider fraud risk, processing costs, and vendor preferences.
How can you prevent unauthorized changes to payment details?
Preventing unauthorized changes to payment details requires strict verification procedures and system controls. Organizations should require vendor change requests to be submitted through formal channels with supporting documentation on vendor letterhead. The AP team must verify all banking changes through callback procedures using phone numbers obtained from independent sources rather than the change request itself.
System access controls should restrict the ability to modify vendor banking information to designated employees who don’t process payments or approve invoices. All changes to payment details should trigger automated alerts to AP management for review and approval. The system should maintain complete audit trails showing who made changes, when they occurred, and what approvals were obtained.
Organizations should implement mandatory waiting periods between banking information changes and the first payment using new details. This delay allows time for verification and reduces the risk of immediate fraudulent payments. Periodic confirmation letters sent to vendor addresses on file help validate that payment information remains accurate and detect unauthorized changes.
What controls are needed for electronic payments and wire transfers?
Electronic payments and wire transfers require enhanced controls due to their speed and irreversibility once executed. Organizations should implement dual authorization requirements where one employee initiates the payment and a second employee with appropriate authority reviews and approves it before transmission. The approver should verify payment details against supporting documentation and confirm the business purpose.
Critical electronic payment controls include:
- Payment amount limits – Require escalating approval levels as payment amounts increase.
- Beneficiary verification – Confirm recipient identity and banking details before first payment.
- Transaction monitoring – Review daily payment reports for unusual patterns or destinations.
- Segregation of duties – Separate payment initiation, approval, and bank account reconciliation functions.
- Callback verification – Contact vendors through known phone numbers to confirm large or unusual payments.
- Cut-off times – Establish deadlines for payment requests to allow proper review before transmission.
Wire transfer controls should include restrictions on authorized recipients, especially for international transfers. Organizations should maintain approved beneficiary lists and require additional authorization for payments to new or infrequent recipients. Same-day wire transfers should require executive approval to ensure adequate review of urgent requests.
How should the check signing authority be managed?
Check signing authority requires clear delegation and physical security controls despite declining check usage. Organizations should designate specific individuals authorized to sign checks based on their position and establish dollar thresholds requiring dual signatures. Signature authority can’t extend to employees who prepare checks, enter vendor information, or reconcile bank accounts.
Physical checks should be stored in locked cabinets with access limited to authorized signers. It’s recommended to number check stock sequentially and keep logs of check ranges and usage. Voided checks must be retained with signatures defaced to prevent fraudulent use.
Many organizations have already transitioned to digital signature platforms that apply authorized signatures electronically or are in the process of doing so. These systems require authentication before applying signatures and maintain audit trails of who signed which checks. Signature specimens should be provided to banks to facilitate verification of checks presented for payment.
What is positive pay, and how does it protect against fraud?
Positive pay is a cash management service offered by banks that matches checks presented for payment against a list of checks the organization has issued. The organization transmits a file to the bank containing check numbers, amounts, and payee names for all checks written. When checks are presented for payment, the bank compares them against this list to flag any discrepancies.
The positive pay process works as follows:
- The organization sends the issued check details to the bank daily or weekly.
- The bank matches presented checks against this file.
- Any exceptions, such as altered amounts or unauthorized check numbers, are flagged and returned to the organization for review.
- The organization then decides whether to pay or return each exception within a specified timeframe.
Positive pay prevents common check fraud schemes, including counterfeit checks, altered payee names, and changed dollar amounts. The service is particularly effective against schemes where fraudsters obtain legitimate check stock and create unauthorized checks using valid account numbers.
Organizations should review exception reports promptly to prevent delays in legitimate payments while blocking fraudulent items. The combination of positive pay and restrictions on check usage creates strong protection against check-based fraud.
How can technology and automation strengthen internal control over accounts payable?
Technology and automation transform internal control over accounts payable from manual, error-prone processes into systematic, enforceable safeguards. Modern AP systems embed control requirements directly into workflows, making it impossible to bypass critical steps. Best practices for accounts payable controls involve using automation to lower fraud risk, increase accuracy, and provide real-time visibility into all payments.
What AP automation tools are available for internal controls?
AP automation tools fall into several categories based on their primary function and control focus.
- End-to-end AP platforms integrate all functions from invoice receipt through payment execution and reconciliation, providing comprehensive control coverage across the entire process. These systems enforce segregation of duties, maintain complete audit trails, and prevent unauthorized access to sensitive functions.
- Specialized automation tools address specific control needs, including OCR for data capture, duplicate detection engines, vendor verification services, and payment fraud prevention systems. Organizations often combine multiple specialized tools with existing ERP systems to create layered control environments tailored to their risk profile.
Tool selection should prioritize integration capabilities with existing financial systems, scalability to handle transaction volume growth, and flexibility to accommodate unique business processes. Organizations must evaluate whether tools provide adequate segregation of duties, support required approval hierarchies, and generate comprehensive reports for monitoring and audit purposes.
Cloud-based solutions typically offer faster implementation and lower upfront costs compared to on-premise systems.
How does OCR technology improve invoice processing accuracy?
Optical character recognition technology uses pattern recognition algorithms to extract data from invoice images and convert it into structured digital information. Modern OCR systems employ ML and AI to improve recognition accuracy over time by learning from corrections made to extraction errors. Advanced systems (like Precoro) achieve accuracy rates exceeding 95% for standard invoice formats.
OCR technology prevents manual data entry errors that occur when employees type invoice information into AP systems. The technology captures key fields, including vendor name, invoice number, date, amount, line item descriptions, and account codes directly from invoice documents. Automated extraction processes invoices in seconds compared to the minutes required for manual entry.
Intelligent OCR systems recognize multiple invoice formats and adapt extraction templates based on vendor-specific layouts. The technology handles various document types, including PDFs, scanned images, emails, and electronic invoices. Organizations should implement validation rules that flag extracted data falling outside expected ranges for manual review. Regular monitoring of OCR accuracy rates (separated by vendor) helps identify situations requiring template adjustments or additional training data.
Can artificial intelligence detect anomalies in AP transactions?
AI invoice processing analyzes patterns across large datasets and identifies deviations from normal behavior. These systems learn typical transaction characteristics, including amounts, frequencies, timing, and vendor relationships. When transactions exhibit unusual patterns, the AI flags them for investigation before payment occurs.
Machine learning models identify sophisticated fraud schemes that rule-based systems miss. The algorithms detect subtle patterns, including gradual invoice increases intended to bypass threshold alerts, vendors whose banking details match employee accounts for reimbursements, and invoice timing that takes advantage of gaps in the approval workflow. AI systems improve detection accuracy as they process more transactions and incorporate feedback on flagged items.
Anomaly detection applications include:
- Identifying duplicate invoices with minor variations
- Recognizing shell company characteristics
- Detecting split invoicing to circumvent approval limits
- Flagging unusual payment destinations or beneficiaries
Organizations should establish processes for investigating AI-generated alerts and documenting resolution decisions. The feedback loop created by human review trains the system to reduce false positives while maintaining high detection rates for genuine anomalies.
What are the benefits of cloud-based AP systems for control?
Cloud-based AP systems provide enhanced control capabilities through centralized data storage, automatic backup, and disaster recovery features that protect against data loss. Cloud platforms maintain complete transaction histories accessible from any location, preventing risks associated with local server failures or physical document loss.
Automatic system updates ensure organizations always operate on current software versions with the latest security patches and control features. Cloud providers commonly use enterprise-grade security measures, including encryption, multi-factor authentication, and intrusion detection, which exceed the capabilities of most individual organizations in this area. Regular third-party security audits of cloud platforms provide independent verification of control effectiveness.
Cloud-based systems facilitate segregation of duties across geographically dispersed teams by centralizing access controls and standardizing policies. Real-time dashboards provide management with immediate visibility into processing status, approval bottlenecks, and control exceptions.
These systems generate comprehensive audit trails automatically without the need for manual log maintenance. Organizations retain data ownership while benefiting from provider expertise in security, backup, and infrastructure management.
How do workflow automation tools enforce approval hierarchies?
Workflow automation enforces approval hierarchies by automatically routing invoices to the right approvers based on predefined criteria, such as amount, department, account code, or vendor. Invoices can’t proceed to payment until all required approvals are completed in the correct sequence. This automated routing also prevents invoices from bypassing approval requirements through manual handling.
The rules engine supports complex approval logic with:
- Dollar thresholds with escalating authority levels
- Department-specific routing
- Requirements for multiple concurrent approvals
Backup approvers can be set in advance to cover situations when primary approvers are unavailable. Software with Approval SLAs enforces approval deadlines and automatically escalates overdue items to management.
Exception handling capabilities let authorized users bypass normal invoice routing in urgent cases, but require documented justification and higher-level approvals. The workflow system keeps a full audit trail, showing who approved each invoice, when it was approved, and the routing path it followed.
Automated notifications alert approvers when invoices require their attention and remind them of pending items approaching the deadline. Organizations can analyze approval patterns to identify bottlenecks, adjust threshold amounts, and optimize workflow configurations for efficiency.
What reconciliation and monitoring procedures are essential?
Implementing key accounts payable controls requires continuous reconciliation and monitoring to ensure internal controls are working as intended and payment data remains accurate.
Regular reconciliations detect errors, prevent fraud, and maintain the integrity of financial statements. Companies must establish systematic review processes that catch issues before they impact financial reporting or create cash flow problems.
How often should accounts payable reconciliations be performed?
Accounts payable reconciliations should occur at multiple frequencies depending on the account type and risk level.
Daily reconciliations focus on high-risk areas, including cash disbursements, wire transfers, and credit card payments. These daily reviews verify that all payments processed match authorized transactions and that no unauthorized activity has occurred.
Weekly reconciliations examine vendor statement comparisons, payment runs, and open invoice aging. Organizations should reconcile payments to approved invoices and verify that all payments clearing the bank correspond to legitimate disbursements. Weekly reviews identify processing errors while they remain fresh and easier to investigate.
Monthly reconciliations provide comprehensive verification that the accounts payable subledger matches the general ledger control account. This process confirms that all invoices, payments, and adjustments have been recorded correctly in both systems.
Monthly procedures should include reconciling vendor statements to internal records, reviewing outstanding credit balances, and confirming that all accruals are properly supported. Quarter-end and year-end reconciliations receive enhanced scrutiny to support financial statement accuracy and audit requirements.
What reports should management review regularly?
Management should review multiple reports on regular schedules to monitor control effectiveness and identify issues requiring attention. The review frequency depends on organizational size, transaction volume, and risk assessment.
Essential management reports include:
- Exception reports – Daily or weekly review of duplicate payments, invoice matching failures, and approval bypasses.
- Aging analysis – Weekly review of outstanding payables by aging bucket to manage cash flow and identify delays.
- Payment activity summaries – Weekly reports showing payment volumes, amounts, and methods by department or vendor.
- Vendor spend analysis – Monthly reports highlighting top vendors, spending trends, and unusual payment patterns.
- Control compliance reports – Monthly verification that segregation of duties, approval limits, and policy requirements are being followed.
- Key performance indicators – Monthly dashboards tracking metrics, such as processing costs, cycle times, and error rates.
- Reconciliation status – Monthly confirmation that all required reconciliations are completed on time and any exceptions are resolved.
Management should establish thresholds that trigger immediate escalation for certain findings, such as suspected fraud, significant reconciliation differences, or control failures. The reports should highlight variances from expected patterns and provide sufficient detail for management to assess whether an investigation is warranted.
How can you identify unusual patterns or exceptions in AP data?
Identifying unusual patterns requires systematic analysis of transaction data against established baselines and expected behaviors. Organizations should use automated exception reporting to flag transactions that meet predefined criteria for potential errors or fraud. The system analyzes patterns across multiple factors, such as amounts, timing, frequency, and relationships.
Key patterns that warrant investigation include:
- Payments consistently below approval thresholds, suggesting deliberate splitting to avoid oversight.
- Vendors receiving payments more frequently than contracted terms indicate.
- Round-dollar invoices that lack the specificity of legitimate charges.
- Sequential invoice numbers from vendors that shouldn’t have such patterns.
- Multiple vendors sharing addresses, phone numbers, or banking information.
- Vendors with names similar to employees or containing generic business terminology.
Organizations should compare current period activity to historical patterns and investigate significant deviations. Sudden increases in payment volumes to specific vendors, new vendors receiving large initial payments, or dormant vendors suddenly reactivated all require explanation. Weekend or holiday payment processing should receive particular scrutiny as fraudsters often exploit periods of reduced oversight.
Exception reports need to find a balance between sensitivity and practicality to catch legitimate issues without overwhelming staff with false positives. Thresholds can be adjusted based on investigation outcomes and changing business conditions. Regularly reviewing errors discovered through other means helps identify gaps in the reporting criteria.
What key performance indicators (KPIs) measure AP control effectiveness?
Key performance indicators provide quantifiable metrics that demonstrate whether internal controls are achieving their intended objectives. Organizations should track KPIs consistently over time and compare results to industry benchmarks and internal targets.
Critical AP control KPIs include:
- Duplicate payment rate – Percentage of total disbursements that are duplicate or erroneous payments.
- Invoice exception rate – Percentage of invoices requiring manual intervention due to matching failures or missing information.
- Days payable outstanding – Average time between invoice receipt and payment, indicating process efficiency.
- Percentage of invoices with purchase orders – Measures compliance with purchasing controls and authorization requirements.
- Straight-through processing rate – Percentage of invoices processed without manual intervention from receipt to payment.
- Average cost per invoice processed – Total AP costs divided by invoice volume, measuring operational efficiency.
- Percentage of payments made on time – Ability to meet vendor terms and capture early payment discounts.
- Vendor master file accuracy rate – Percentage of active vendors with complete, verified information.
Organizations should establish target ranges for each KPI based on industry standards and internal capabilities. Significant variances from targets should trigger root cause analysis and corrective action. KPI trends over multiple periods reveal whether control improvements are having desired effects or if performance is deteriorating.
Why is aging analysis important for payables management?
Aging analysis categorizes outstanding payables into time-based buckets that show how long invoices have remained unpaid since their due dates. Standard aging buckets include current, 1-30 days past due, 31-60 days past due, 61-90 days past due, and over 90 days past due. This analysis provides immediate visibility into payment timing and helps organizations prioritize payments and manage cash flow.
From a control perspective, aging analysis identifies invoices stuck in the approval process, payments delayed by processing errors, and disputes preventing payment. Invoices aging beyond normal terms may indicate approval bottlenecks, missing documentation, or unresolved discrepancies that require attention. Unusual aging patterns separated by vendor or department can reveal systematic control weaknesses or compliance failures.
Aging analysis supports cash flow forecasting by showing upcoming payment obligations and helping organizations plan liquidity needs. Management can identify opportunities to capture early payment discounts for current invoices or negotiate payment terms for aged balances.
Analysis can also identify vendors offering informal credit by delaying collections, which may signal relationship issues or dissatisfaction with payment practices. Regular review of aging balances helps organizations maintain strong vendor relationships while managing working capital effectively.
How does the month‑end close impact accounts payable controls?
Month-end close creates heightened control requirements due to the need for accurate financial reporting and proper period cutoff. Organizations must ensure that all invoices are recorded in the correct accounting period and that accruals properly reflect goods or services received but not yet invoiced. Month-end timing pressures can increase risk when controls are intentionally relaxed to meet reporting deadlines.
Proper cutoff procedures verify that invoices are recorded in the period when the related goods were received or services performed, not simply when the invoice arrived or was processed. Organizations should implement controls that prevent backdating invoices or manipulating transaction dates to achieve desired financial results. Receiving reports and service completion records determine the correct period for recognizing expenses, regardless of when invoices arrive.
Month-end reconciliations are closely reviewed to ensure the accounts payable subledger matches the general ledger control accounts. All invoices entered during the period must be properly approved, coded, and recorded before close.
Companies need to review accruals for reasonableness and ensure supporting documentation exists for all material estimates. The reconciliation process identifies and resolves discrepancies before financial statements are finalized.
Controls should not be bypassed or weakened to meet close deadlines. Management must allocate sufficient time and resources to complete proper control procedures during the month-end period. Organizations that consistently miss close deadlines should assess whether staffing, processes, or systems need improvement, instead of weakening internal controls to meet the schedule.
How do you conduct an accounts payable internal controls assessment?
An accounts payable internal controls assessment systematically evaluates whether existing procedures are properly designed and functioning as intended. A comprehensive review examines AP risks and processes to identify gaps before they result in financial losses.
Regular assessments ensure that internal control over accounts payable remains effective as business evolves and grows. Organizations should perform assessments annually with targeted reviews more frequently for high-risk areas.
What should be included in an accounts payable key controls audit checklist?
An AP audit checklist should cover all critical control areas and provide specific items for verification. It guides assessors through a systematic review of preventive and detective measures across the accounts payable process.
Segregation of duties:
- Verify separation between vendor setup, invoice approval, payment processing, and reconciliation functions.
- Confirm that no single employee can create vendors and process payments.
- Review system access rights to ensure appropriate restrictions.
- Test whether backup procedures maintain segregation when primary staff is unavailable.
Authorization and approval controls:
- Verify approval hierarchies are documented and current.
- Test whether dollar thresholds are enforced by system controls.
- Confirm supervisory review occurs before payments are released.
- Review evidence of proper authorization for exceptions and overrides.
Vendor management:
- Verify vendor onboarding procedures include proper documentation and verification.
- Test the vendor master file for duplicate records and inactive vendors.
- Confirm banking information changes follow verification protocols.
- Review periodic vendor file maintenance and cleanup procedures.
Invoice processing:
- Verify that three-way matching is performed, and exceptions are investigated.
- Test whether invoices without purchase orders receive enhanced scrutiny.
- Confirm proper coding and allocation to general ledger accounts.
- Review documentation requirements and retention practices.
Payment controls:
- Verify dual authorization for electronic payments and wire transfers.
- Test positive pay or similar fraud prevention mechanisms for checks.
- Confirm payment methods are secure and appropriate for transaction types.
- Review reconciliation procedures for all payment accounts.
Monitoring and reporting:
- Verify exception reports are generated and reviewed regularly.
- Test whether unusual transactions are investigated and resolved.
- Confirm management receives and reviews the required reports.
- Review key performance indicators and trend analysis.
How do you identify weaknesses in your current AP processes?
Identifying weaknesses requires comprehensive analysis using multiple assessment techniques. Organizations should combine document review, personnel interviews, transaction testing, and data analytics to build a complete picture of control effectiveness. The assessment should examine both control design and operating effectiveness.
First, review written policies and procedures to understand how controls should function. Compare documented procedures to actual practices through observation and employee interviews. This comparison often reveals situations where controls exist on paper but aren’t followed in practice, or where informal workarounds bypass intended controls.
Transaction testing provides evidence of whether controls operate effectively. Select samples of invoices, payments, and vendor records to verify that required approvals were obtained, supporting documentation exists, and proper procedures were followed. Testing should include both normal transactions and exceptions to ensure that controls function under various circumstances.
Data analytics identifies patterns indicating potential control weaknesses. Analyze payment data for red flags, such as duplicate payments, vendors with sequential invoice numbers, round-dollar amounts, or payments just below approval thresholds. Review vendor master file data for duplicate records, multiple vendors at the same address, or incomplete information. Exception reports should highlight transactions that deviate from expected patterns.
Key indicators of control weaknesses include:
- Recurring reconciliation differences or delays in completing reconciliations.
- High rates of invoice exceptions or matching failures.
- Frequent emergency payments or rush processing outside normal procedures.
- Large numbers of manual journal entries or adjustments.
- Employee complaints about process inefficiencies or unclear procedures.
Document all identified weaknesses with sufficient detail to support recommendations for improvement. Assess the severity of each weakness based on its potential financial impact and likelihood of occurrence. Prioritize remediation efforts according to the risk assessment and available resources. Follow-up assessments should verify that corrective actions have been implemented effectively and are achieving intended results.
How do AP controls contribute to supply chain diversification and resilience?
AP controls provide critical data and visibility that support supply chain diversification strategies and resilience planning. Payment data reveals vendor concentration risks when large percentages of spend flow to single suppliers or limited vendor groups. Organizations can also analyze payment patterns in order to identify dependencies on specific vendors for critical goods or services.
Vendor master file data allows organizations to track vendor locations, ownership structures, and geographic concentration. It helps identify cases where seemingly separate vendors are actually related entities or subsidiaries of the same parent company.
This visibility makes it easier to assess whether diversification strategies are genuine or if concentration risk remains. Payment analytics further reveal spending patterns, guiding decisions on expanding the vendor base or developing alternative supply sources.
Controls that verify vendor legitimacy and financial stability contribute to supply chain resilience in their own way: they reduce risks of vendor failures or fraud. Organizations that maintain current vendor information (insurance coverage, financial condition, and operational capabilities) can better anticipate and respond to supply disruptions. Regular vendor performance reviews, using payment data, help distinguish vendors who consistently meet their obligations from those that need closer monitoring.
Business continuity planning benefits from AP system controls that ensure payment capabilities continue during disruptions. Organizations with cloud-based AP systems, backup payment methods, and documented procedures can maintain vendor payments even when primary operations are disrupted. The ability to pay vendors reliably during crises also helps maintain both supply chain relationships and operational continuity.
Frequently asked questions
An accounts payable policy manual should outline segregation of duties, approval hierarchies, vendor management procedures, invoice processing steps, payment authorization protocols, and document retention policies. It should be reviewed annually or after significant business, regulatory, or organizational changes, with updates communicated to employees and training provided as needed.
AP automation tools support remote work by giving cloud-based access to invoice processing, approvals, and payment authorization from anywhere. Electronic document management removes the need for physical invoices and lets multiple team members review and process documents at the same time. Automated workflows route invoices to the right approvers, maintain full audit trails, and enforce all required controls.
Key indicators of effective AP internal controls are duplicate payment rates below 0.5% of total disbursements, invoice exception rates under 10%, and days payable outstanding within industry benchmarks. Additional metrics include straight-through processing rates above 70%, vendor master file accuracy exceeding 95%, and on-time payment rates above 90%. Organizations should also track the cost per invoice processed and monitor trends over time to ensure controls maintain effectiveness without creating operational inefficiencies.
Strengthen your internal controls, gain full visibility into vendor risk, and build a more resilient supply chain. Book your personalized Precoro demo today.